Data Cyber Security: A Comprehensive Approach to Mitigating Digital Risks
Data Cyber Security: A Comprehensive Approach to Mitigating Digital Risks
Blog Article
The Important Duty of Information and Network Safety in Shielding Your Details
In an age where data violations and cyber dangers are progressively prevalent, the relevance of durable data and network safety can not be overstated. The implementation of efficient safety and security actions, such as security and gain access to controls, is essential to preserving count on and operational stability.
Comprehending Data Safety
In today's electronic landscape, an overwhelming majority of companies come to grips with the complexities of data protection. This essential component of infotech entails securing sensitive data from unauthorized gain access to, corruption, or burglary throughout its lifecycle. Information safety incorporates various techniques and innovations, consisting of file encryption, access controls, and data masking, all targeted at protecting info versus violations and susceptabilities.
An essential facet of information security is the identification and category of data based upon its sensitivity and importance. This category helps organizations prioritize their security efforts, allocating sources to shield one of the most crucial info efficiently. Furthermore, applying durable policies and procedures is important to ensure that employees recognize their duty in maintaining information safety.
Normal audits and assessments aid in identifying possible weak points within an organization's information safety framework. In addition, staff member training is important, as human mistake continues to be a considerable consider information breaches. By fostering a culture of safety recognition, organizations can minimize risks connected with expert threats and oversight.
Significance of Network Safety And Security
Network safety and security stands as a foundation of a company's overall cybersecurity method, with about 90% of services experiencing some type of cyber hazard over the last few years. The significance of network safety lies in its capability to secure delicate details and preserve the integrity of organization operations. By securing network infrastructures, companies can avoid unapproved access, data violations, and various other destructive tasks that could threaten their possessions and online reputation.
Carrying out robust network protection measures not only assists in mitigating dangers but additionally fosters trust among clients and stakeholders. When consumers are guaranteed that their economic and individual information is safe and secure, they are most likely to involve with the organization, causing boosted customer commitment and service development.
Moreover, a well-structured network safety structure facilitates conformity with various regulative demands. Organizations should adhere to industry criteria and lawful mandates worrying data defense, and reliable network safety and security techniques can ensure conformity, therefore preventing prospective penalties.

Typical Cyber Hazards
Organizations should continue to be attentive versus a range of cyber threats that can undermine their network protection efforts. Among the most typical dangers is malware, which incorporates infections, worms, and ransomware that can disrupt operations, take data, or hold information hostage. Phishing attacks, where destructive stars impersonate trusted entities to deceive people right into revealing sensitive information, remain to expand in class, making individual education and learning vital.
One more common danger is distributed denial-of-service (DDoS) assaults, which overload systems with website traffic, providing them inaccessible to genuine individuals. Expert hazards, whether unintended or deliberate, pose substantial dangers as workers may inadvertently reveal delicate information or intentionally manipulate their accessibility for harmful functions.
Additionally, vulnerabilities in software and hardware can be made use of by cybercriminals, highlighting the relevance of routine updates and patch administration. Social engineering strategies further make complex the landscape, as attackers adjust individuals right into revealing confidential details through mental manipulation.
As these hazards develop, organizations have to preserve a proactive method to recognize, mitigate, and respond successfully to the ever-changing cyber threat landscape, protecting their useful details and maintaining depend on with stakeholders. fft pipeline protection.
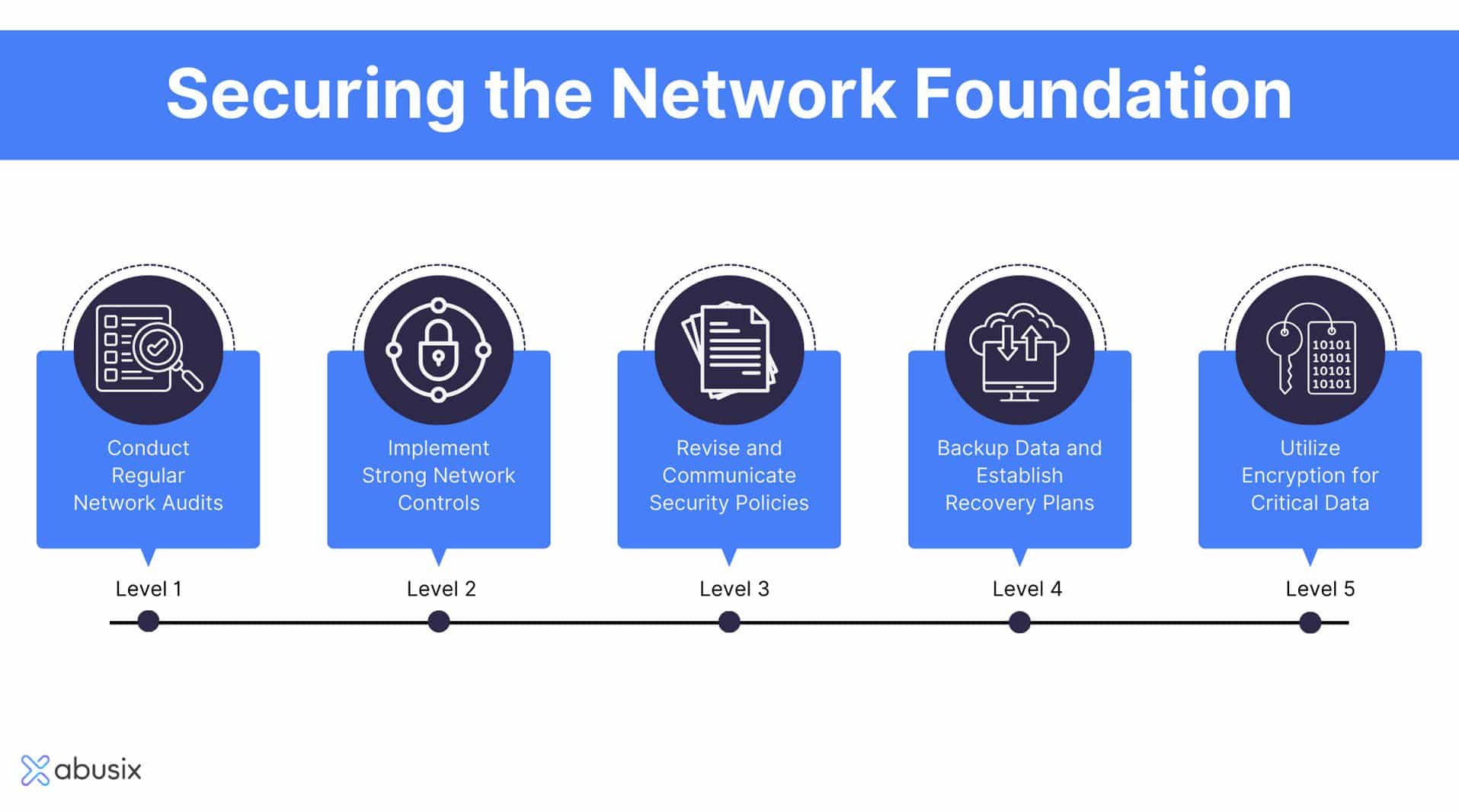
Finest Practices for Security
Executing robust protection measures is essential for guarding sensitive info and keeping functional integrity. Organizations must begin by performing extensive danger evaluations to recognize vulnerabilities within their systems. This aggressive method allows the prioritization of protection efforts customized to the specific requirements of the company.
Taking on solid password policies is important; passwords need to be complex, routinely altered, and handled utilizing protected password monitoring tools. Multi-factor verification (MFA) adds an added layer of safety by needing extra confirmation approaches, therefore minimizing the threat of unauthorized access.
Normal software program updates and spot management are critical to safeguard against known susceptabilities. Implementing firewall programs and invasion discovery systems can further shield networks from external risks. Worker training is similarly crucial; team needs to be educated on identifying phishing attempts and recognizing the fiber network security relevance of information security procedures.
Information encryption ought to be used for sensitive details, both at remainder and in transit, to make sure that also if information is obstructed, it continues to be unattainable (fft pipeline protection). Lastly, organizations should establish and frequently test event feedback prepares to make sure speedy activity in case of a security breach. By sticking to these finest techniques, organizations can enhance their security posture and protect their essential information assets
Future Trends in Security
The landscape of information and network safety is constantly developing, driven by improvements in modern technology and the increasing refinement of cyber risks. As companies progressively take on cloud computer and IoT gadgets, the standard of safety and security will certainly shift towards a zero-trust design. This strategy stresses that no entity-- inner or outside-- is naturally relied on, mandating verification at every accessibility factor.
Moreover, the use of expert system and artificial intelligence in security procedures gets on the increase. These technologies make it possible for anticipating analytics, permitting companies to recognize vulnerabilities and potential risks before they can be exploited. Automation will likely play a critical function in improving security reactions, reducing the time taken to minimize violations.
In addition, regulatory frameworks will remain to tighten, necessitating more rigid compliance measures. Organizations should stay abreast of evolving policies to ensure they meet protection standards.
Conclusion
Finally, the importance of information and network protection can not be overstated in the contemporary digital landscape. With the prevalence of cyber dangers and the increasing complexity of regulatory requirements, organizations should take on detailed safety and security measures to secure sensitive details. By remaining and implementing efficient strategies educated about emerging trends, organizations can enhance their resilience versus possible assaults, making sure information integrity and fostering depend on amongst stakeholders and clients. Focusing on security remains vital for functional connection and long-term success.
In an age where data breaches and cyber hazards are significantly common, the value of robust data and network security can not be overemphasized. Data safety and security includes different methods and modern technologies, consisting of encryption, access controls, and data masking, all aimed at guarding info versus violations and vulnerabilities.
A basic facet of data safety is the identification and classification of information based on its sensitivity and importance.The landscape of data and network protection is constantly developing, driven by developments in technology and the raising sophistication of cyber threats.In verdict, the significance of data and network protection can not be overstated in the contemporary electronic landscape.
Report this page